Information security
fromComputerWeekly.com
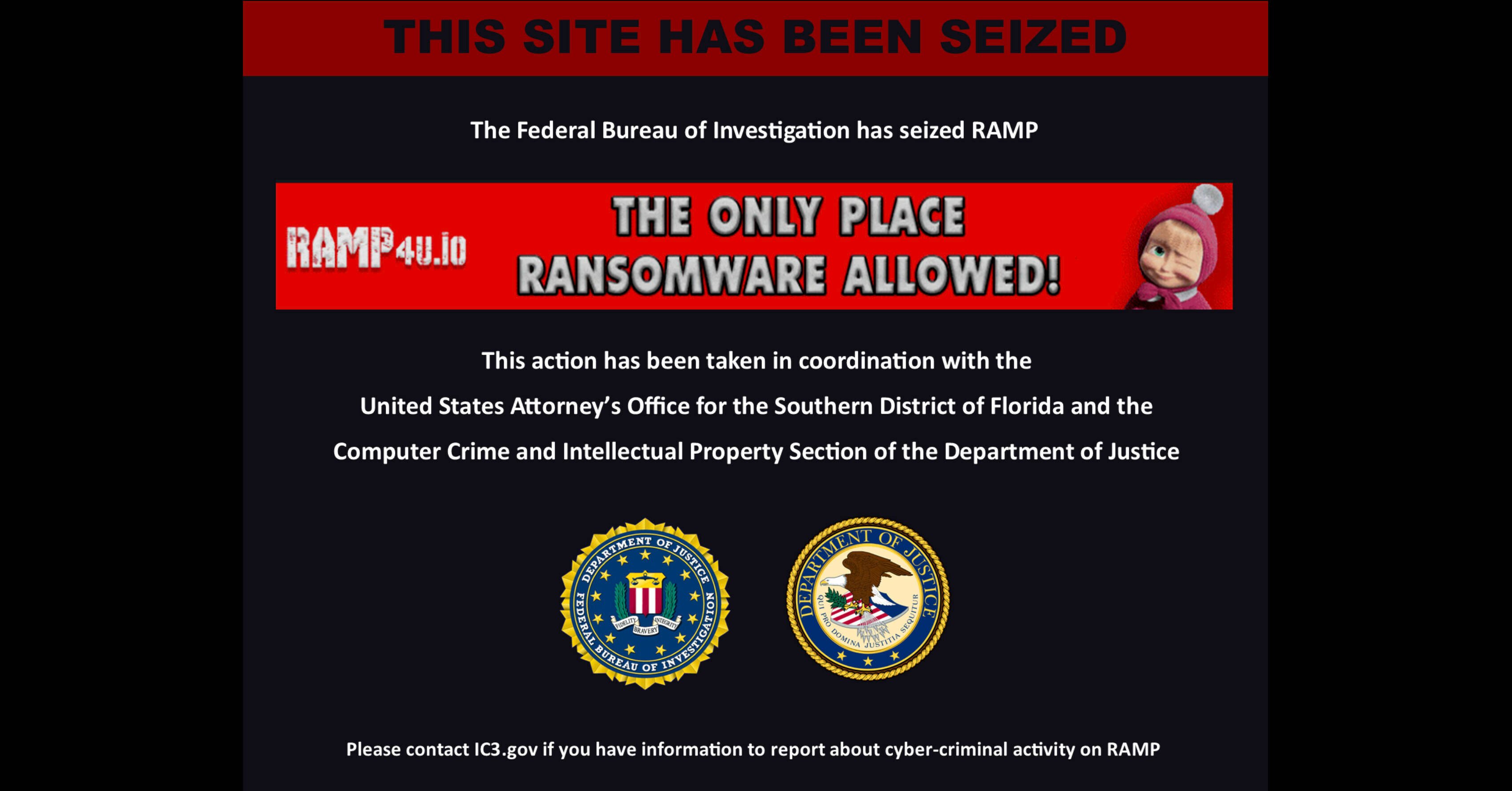
10 hours agoRansomware gangs focus on winning hearts and minds | Computer Weekly
Ransomware gangs are professionalizing, scaling affiliate models, recruiting insiders and cyber professionals, and offering larger commissions and better OpSec to enable more successful attacks.